A Practical Guide to Burp Suite
12/12/2024 | Billie Crabtree - Partner, Head of Operations - Ethan Leitner - Partner, Security Specialist

What is Burp Suite?
Burp Suite is a comprehensive toolkit for web application security testing. It is primarily used for intercepting, analyzing, and modifying HTTP request packets but its capabilities extend far beyond that. Key features include:
- Intercepting and modifying HTTP requests and responses.
- Fuzzing endpoints with wordlists to discover hidden resources.
- Manipulating query parameters, headers, and other request attributes.
- Sending precise sequences of crafted packets to target hosts for testing purposes.
HTTP requests are the backbone of the web, facilitating the transfer of data between servers and browsers. For example, if you were to submit a form on a website, your browser would send a POST request to a backend API at the appropriate endpoint, setting any required headers or cookies to authenticate with the server.
Getting Started with the Proxy
While this guide does not cover installation (installation steps are available here), setting up Burp Suite is straightforward. Once installed, the Proxy tab is the starting point. This feature allows you to intercept and modify HTTP traffic in real-time. Here’s a quick walkthrough:
- Open the browser within Burp Suite (a customized version of Chrome integrated with the tool).
- Navigate to the website you want to test and enable the “Intercept” option.
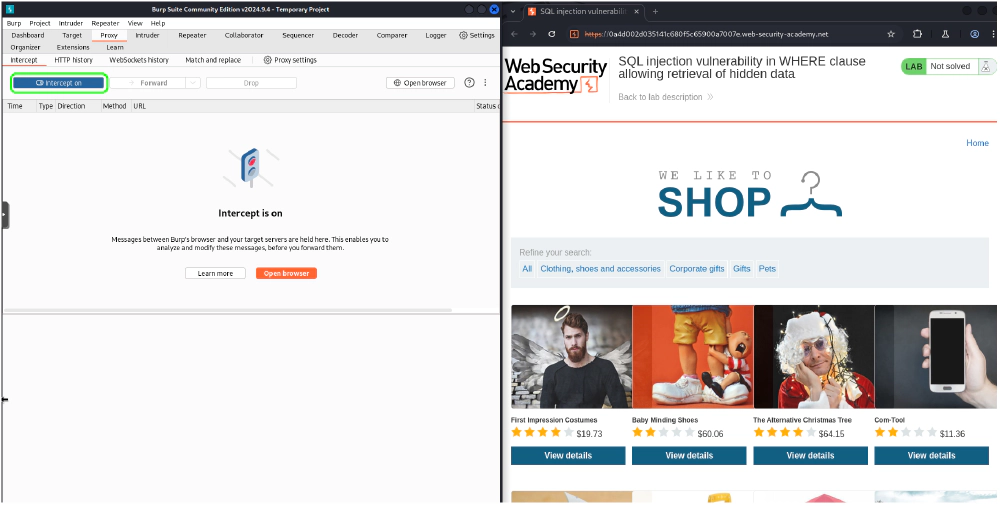
Tip: If the intercept is on but you’re stuck waiting for a page to load, you may need to temporarily disable the intercept, navigate to your desired page, and then re-enable it.
When you capture a request, it will appear in the request panel at the bottom left of the Proxy tab. From there, you can:
- Modify the endpoint being accessed.
- Edit body parameters or JSON payloads.
- Alter headers or cookies to test different scenarios.
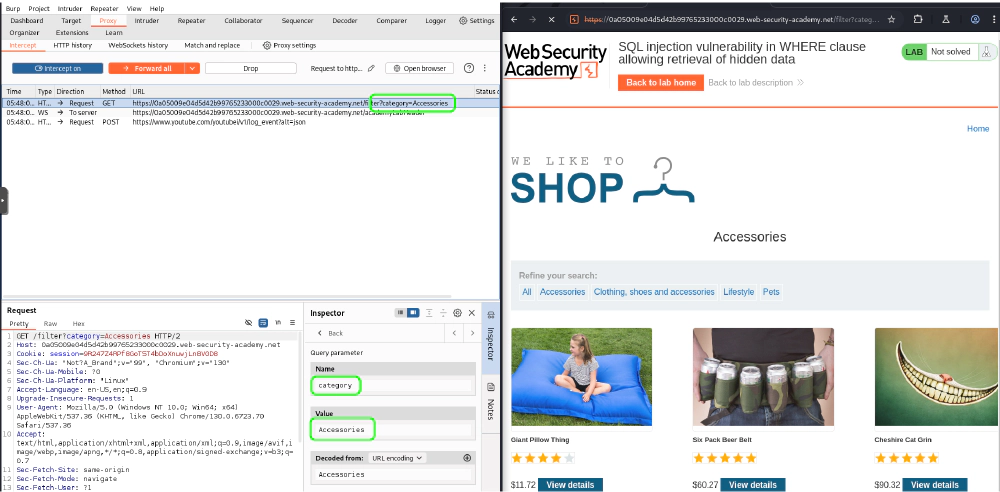
Once you’ve captured and modified a request, you can send it to other Burp Suite tools for deeper analysis, for example, the Repeater.
The Burp Repeater
The Repeater is ideal for testing requests that can be repeatedly sent with different parameters. This is particularly useful for:
- Examining how servers handle various inputs.
- Identifying vulnerabilities by altering payloads incrementally.
To use the Repeater:
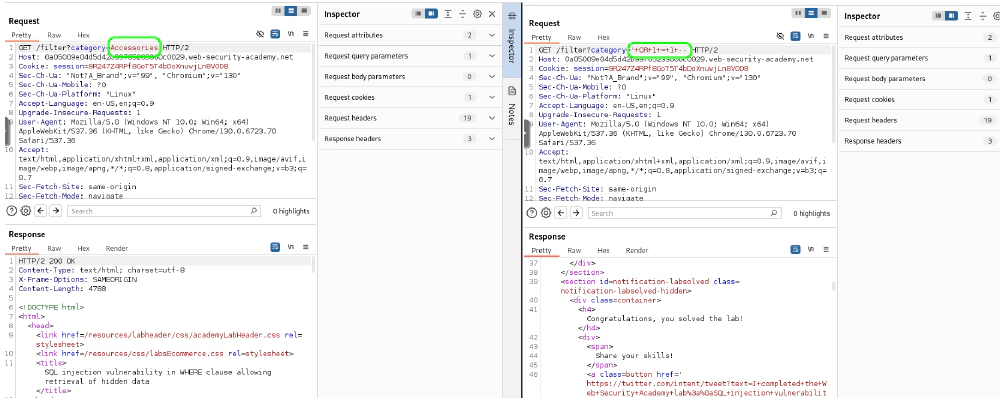
- Right-click a request in the Proxy tab and select Send to Repeater.
- In the Repeater tab, you can freely modify the request and resend it to observe the server’s response.
The Burp Intruder
The Intruder automates testing by sending a series of payloads to specific parts of a request. This is particularly useful for:
- Fuzzing endpoints to discover hidden resources.
- Testing parameter values to uncover vulnerabilities like SQL injection or XSS.
How to Use the Intruder:
- Highlight the portion of the request you want to modify (e.g., a parameter or a part of the URL).
- Right-click and select Add Payload Position.
- Navigate to the payload configuration panel:
- Select a wordlist to use as your payload source.
- Optionally, add processing steps (e.g., HTTP encoding payloads).
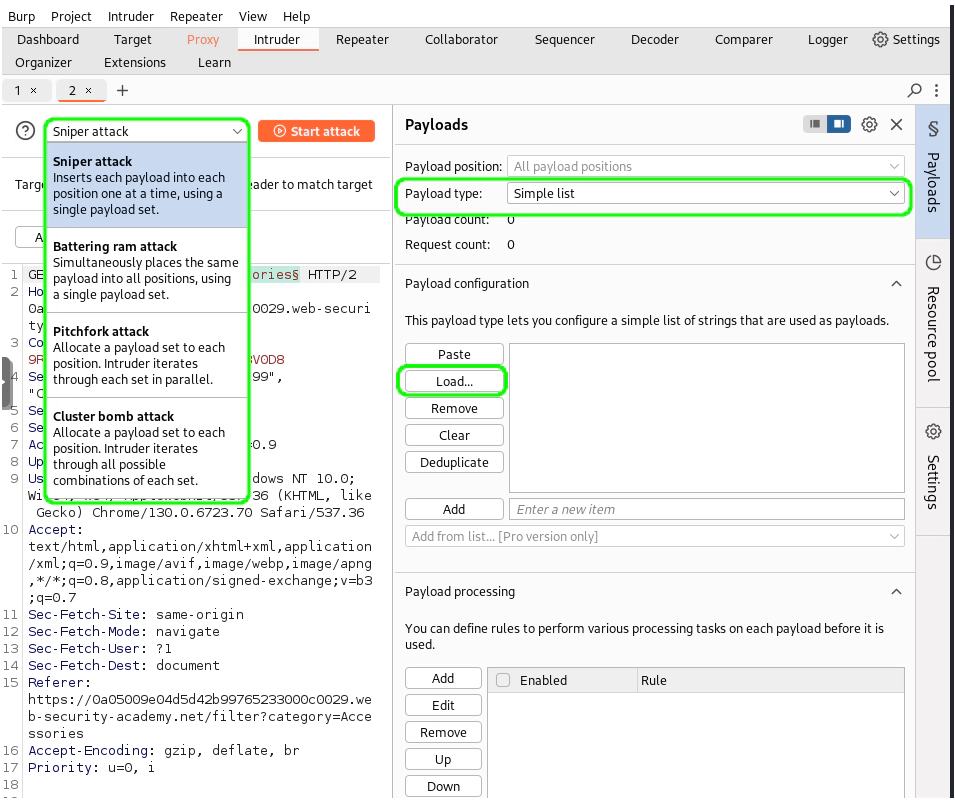
The Intruder is an excellent choice for fuzzing if you’re new to tools like ffuf, providing a user-friendly interface with robust capabilities.
Conclusion
Burp Suite is a powerful and versatile tool for web application security testing. Whether you’re intercepting traffic, modifying requests, or fuzzing endpoints, it provides an intuitive yet feature-rich environment for web application investigation and exploitation. By mastering its core tools like the Proxy, Repeater, and Intruder you’ll be well-equipped to identify and address common web application vulnerabilities effectively.


